About cookies on this site Our websites require some cookies to function properly (required). In addition, other cookies may be used with your consent to analyze site usage, improve the user experience and for advertising. For more information, please review your options. By visiting our website, you agree to our processing of information as described in IBM’sprivacy statement. To provide a smooth navigation, your cookie preferences will be shared across the IBM web domains listed here.
Abstract
Looking at the pervasiveness of encryption today, you can understand the challenge an organization faces with managing the cryptography infrastructure and the encryption keys and certificates for their IT infrastructures. Financial institutions use encryption to secure payments as they face compliance requirements from the Payment Card Industry (PCI): the PCI-PIN and PCI-DSS requirements. Other organizations have to deal with the protection of personal data, for example, the public sector, insurance companies, and healthcare providers. They must comply with complex regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) and the Data Protection Directive 95/46/EC.
This IBM® Redbooks® Solution Guide describes the IBM Enterprise Key Management Foundation. By using it, organizations can centralize the key management effort and, in this way, simplify their key management processes. Simplified and unified processes are an important step toward compliance. Figure 1 shows the IBM Enterprise Key Management Foundation overview.
Contents
Looking at the pervasiveness of encryption today, you can understand the challenge an organization faces with managing the cryptography infrastructure and the encryption keys and certificates for their IT infrastructures. Financial institutions use encryption to secure payments as they face compliance requirements from the Payment Card Industry (PCI): the PCI-PIN and PCI-DSS requirements. Other organizations have to deal with the protection of personal data, for example, the public sector, insurance companies, and healthcare providers. They must comply with complex regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) and the Data Protection Directive 95/46/EC. This IBM® Redbooks® Solution Guide describes the IBM Enterprise Key Management Foundation. By using it, organizations can centralize the key management effort and, in this way, simplify their key management processes. Simplified and unified processes are an important step toward compliance. Figure 1 shows the IBM Enterprise Key Management Foundation overview.
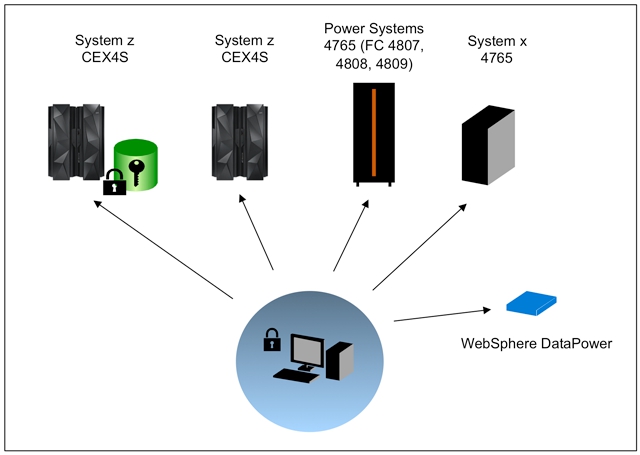
Figure 1. IBM Enterprise Key Management Foundation overview
The IBM Enterprise Key Management Foundation is built around a workstation that utilizes a key management application and an IBM 4765 cryptographic co-processor for secure key generation. The other main component in the IBM Enterprise Key Management Foundation is the key repository, an IBM DB2® database that is often deployed on an IBM z/OS® system. From the workstation, keys are pushed to the supported platforms shown in Figure 1.
Did you know?
The IBM Enterprise Key Management Foundation is policy driven and, as such, provides separation of duties. It can be configured to require two or more people to log on, and all key management activities are logged in a central log in DB2, and optionally in SMF on z/OS, as well. These capabilities make it easier to demonstrate compliance during audits.
Monitoring and reporting facilities are available and the key managers can issue key management requests from their desktop computers. Later, these requests can be executed in the secure environment of the IBM Enterprise Key Management Foundation workstation, in this way providing an efficient key management workflow.
Business value and solution overview
The IBM Enterprise Key Management Foundation provides business value for all organizations that have to manage and maintain encryption keys in their IT infrastructure:
Others who read this also read
Special Notices
The material included in this document is in DRAFT form and is provided 'as is' without warranty of any kind. IBM is not responsible for the accuracy or completeness of the material, and may update the document at any time. The final, published document may not include any, or all, of the material included herein. Client assumes all risks associated with Client's use of this document.
