Abstract
Cybercrime is a sophisticated activity. It is no longer a playing field for “script-kiddies” trying to get access to systems and servers for fun, and it is not about quick hacks to get in and get out quickly. It is now about real commercial, political, or even military advantages. There have been reports in the press recently of large systems data breaches, and it is apparent that some of these are associated with attempts to access mainframe data.
The skills and knowledge that are required to manage and operate a sophisticated IBM System z mainframe are different from those that are used by professionals who use Linux, UNIX, or Windows servers for commercial organizations. The complexity of ways in which various organizations use System z over many years, means that there are now fewer people with the knowledge and skills to even attempt breaking into a mainframe system. However, as criminal organizations realize the benefits of gaining access to mainframe data, the efforts to achieve this increase. The requirement to secure mainframes and their valuable data exists within every organization, within a network of firewalls and network protection systems, access control hubs, DMZs, and application gateways, all of which can make up layers of defense.
In consequence, it is of real value for us to consider the security capabilities of the mainframe. This time, however, we want to ensure that you know how to configure these machines so that they are highly resistant to attacks. If resistance is not possible or practical, you must understand where detective controls can be used. If detective controls are not possible, then you must understand what forensic capabilities are possible. This IBM Redbooks Solution Guide provides the security professional, or the enterprise security architect, an understanding of best practices to secure the IBM mainframe in a holistic approach.
Contents
Cybercrime is a sophisticated activity. It is no longer a playing field for “script-kiddies” trying to get access to systems and servers for fun, and it is not about quick hacks to get in and get out quickly. It is now about real commercial, political, or even military advantages. There have been reports in the press recently of large systems data breaches, and it is apparent that some of these are associated with attempts to access mainframe data.
The skills and knowledge that are required to manage and operate a sophisticated IBM System z mainframe are different from those that are used by professionals who use Linux, UNIX, or Windows servers for commercial organizations. The complexity of ways in which various organizations use System z over many years, means that there are now fewer people with the knowledge and skills to even attempt breaking into a mainframe system. However, as criminal organizations realize the benefits of gaining access to mainframe data, the efforts to achieve this increase. The requirement to secure mainframes and their valuable data exists within every organization, within a network of firewalls and network protection systems, access control hubs, DMZs, and application gateways, all of which can make up layers of defense. See Figure 1.
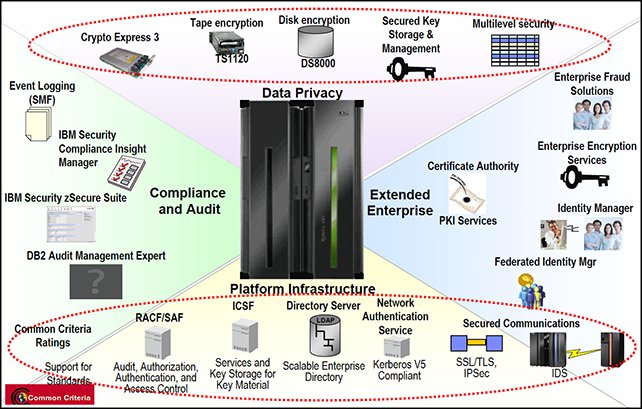
Figure 1. Elements of Enterprise Security
In consequence, it is of real value for us to consider the security capabilities of the mainframe. This time, however, we want to ensure that you know how to configure these machines so that they are highly resistant to attacks. If resistance is not possible or practical, you must understand where detective controls can be used. If detective controls are not possible, then you must understand what forensic capabilities are possible. This IBM Redbooks Solution Guide provides the security professional and the enterprise security architect with an understanding of best practices to secure the IBM mainframe in a holistic approach.
Did you know?
Very often you hear that IBM z/OS running on System z is the most secure commercial operating system available. We (the authors) beg to disagree. If configured properly, it is as secure as claimed. Many audits that are performed in System z environments are executed with a light touch. Some management teams are happy with this approach because they have a natural desire to pass audits. A passed audit typically signals that everything is working well and as designed. However, this approach can instill a false sense of security. While System z is inherently resistant to hacking and information theft because of the controls built into its hardware microcode to support process isolation and data integrity, it can also be configured and run in a highly insecure manner. So, we might more accurately claim that z/OS is the most securable commercial operating system available.
The 1973 MVS statement of integrity has formed the basis for more than three decades of the MVS successors’ industry leadership in system security. The fact that IBM was able to make such emphatic claims so early in the life of the MVS family of operating systems, and has been able to maintain that claim for all the years since, speaks volumes for the stability and reliability of the hardware and software. The z/OS “System Integrity” is defined as the inability of any program that is not authorized by a mechanism under the installation’s control to circumvent or disable store or fetch protection, access a resource that is protected by the z/OS Security Server (RACF), or obtain control in an authorized state. The current z/OS statement of integrity can be found at the following website:
http://www.ibm.com/systems/z/os/zos/features/racf/zos_integrity_statement.html
With the statement of integrity, IBM also commits to address and resolve any system integrity problem that is reported.
Business value
Hacking is only part of the process to gain access to enterprise data with malicious intent. If access to one part of an enterprise IT environment is gained, then this access can be used to extend access to another part. The initial breach of the security controls is used to create or obtain another breach. Usually, data is leaked carefully over a long period of time. Breaches are used and controlled by attackers so that detection is difficult. This level of activity is no longer associated only with distributed servers, which frequently run Linux, UNIX, or Windows based software. The goal in many of these attacks is to access the data that is held on the mainframe, also called the System of Record. Why would the mainframe be under attack? Well, many years ago, the infamous American bank robber John Dillinger was asked why he robbed banks. He replied, “Because that is where the money is.” So, the answer to why the mainframe is now under attack is that this is the server where many organizations store and process their most valuable data.
The System z mainframe might be running z/VM to host Linux servers. There might be one or more z/OS LPARs in one sysplex, even with z/OS under z/VM for testing or software maintenance purposes. There are many aspects to the security of such an environment. To protect such an environment, you must consider the following subjects:
Others who read this also read
Special Notices
The material included in this document is in DRAFT form and is provided 'as is' without warranty of any kind. IBM is not responsible for the accuracy or completeness of the material, and may update the document at any time. The final, published document may not include any, or all, of the material included herein. Client assumes all risks associated with Client's use of this document.
